STM32MP15 secure boot
目录
Purpose
Secure boot is a key feature to guarantee a secure platform.
STM32MP1 boot sequence supports a trusted boot chain that ensures that the loaded images are authenticated and checked in integrity before being used.
| The secure boot feature availability is indicated in the security field of the chip part number. |
Authentication processing
STM32 MPU provides authentication processing with ECDSA [1] verification algorithm, based on ECC [2]. ECDSA offers better result than RSA with a smaller key. STM32 MPU relies on a 256 bits ECDSA key.
Two algorithms are supported for ECDSA calculation:
- P-256 NIST
- Brainpool 256
The algorithm selection is done via the signed binary header, as shown in STM32 header (subchapter in this same article).
The EDCSA verification follows the process below:
Key generation
First step is to generate the ECC pair of keys with STM32 KeyGen tool. This is the key pair that will be used to sign the images.
The tool also generates a third file containing the public key hash (PKH) that will be used to authenticate the public key on the target.
Key registration
| Make sure that a device with Secure boot enabled is used: this is mentionned in the part number, otherwise the device will become permanently unusable. |
Register hash public key
First step to enable the authentication is to burn the OTP WORD 24 to 31 in BSEC with the corresponding public key hash (PKH, output file from STM32 KeyGen).
OpenSTLinux embeds a stm32key tool that can be called from U-Boot command line interface to program the PKH into the OTP.
PKH file (publicKeyhash.bin) must be available in a filesystem partition (like bootfs) on a storage device (like sdcard) before proceeding.
Board $> ext4load mmc 0:4 0xc0000000 publicKeyhash.bin Load hash file from mmc 0 partition 4 (ext4) in DDR
32 bytes read in 50 ms (0 Bytes/s)
Board $> stm32key read 0xc0000000 Read loaded key from DDR to confirm it is valid (without writing it in OTP)
OTP value 24: 12345678
OTP value 25: 12345678
OTP value 26: 12345678
OTP value 27: 12345678
OTP value 28: 12345678
OTP value 29: 12345678
OTP value 30: 12345678
OTP value 31: 12345678
| If hash key is ok, the key in OTP can be fused |
Board $> stm32key fuse -y 0xc0000000 Write the key in OTP
The device now contains the hash to authenticate images. To read back the OTP, you can use NVMEM framework.
Image signing
In a second step, FSBL and SSBL binaries must be signed. STM32 Signing tool allows to fill the STM32 binary header that is parsed by the embedded software to authenticate each binary.
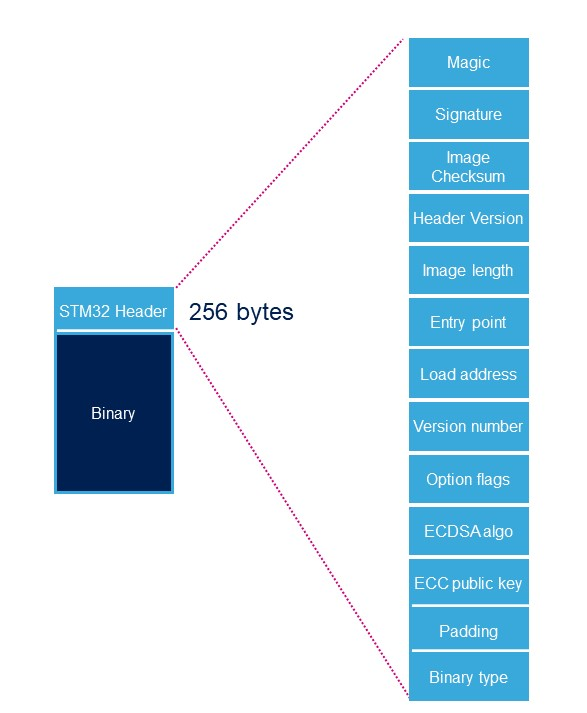
STM32 Header
由ROM code 和 TF-A 加载的每个二进制映像(已签名或未签名)都需要在二进制数据的顶部添加特定的STM32标头,标题包括认证信息。
| Name | Length | Byte Offset | Description |
|---|---|---|---|
| Magic number | 32 bits | 0 | 4 bytes in big endian: 'S', 'T', 'M', 0x32 = 0x53544D32 |
| Image signature | 512 bits | 4 | ECDSA signature for image authentication[Note 1] |
| Image checksum | 32 bits | 68 | Checksum of the payload[Note 2] |
| Header version | 32 bits | 72 | Header version v1.0 = 0x00010000 Byte0: reserved Byte1:major version = 0x01 Byte2: minor version = 0x00 Byte3: reserved |
| Image length | 32 bits | 76 | Length of image in bytes[Note 3] |
| Image entry Point | 32 bits | 80 | Entry point of image |
| Reserved1 | 32 bits | 84 | Reserved |
| Load address | 32 bits | 88 | Load address of image[Note 4] |
| Reserved2 | 32 bits | 92 | Reserved |
| Version number | 32 bits | 96 | Image Version (monotonic number)[Note 5] |
| Option flags | 32 bits | 100 | b0=1: no signature verification[Note 6] |
| ECDSA algorithm | 32 bits | 104 | 1: P-256 NIST ; 2: brainpool 256 |
| ECDSA public key | 512 bits | 108 | ECDSA public key to be used to verify the signature.[Note 7] |
| Padding | 83 Bytes | 172 | Reserved padding bytes[Note 8]. Must all be set to 0 |
| Binary type | 1 Byte | 255 | Used to check the binary type 0x00: U-Boot 0x10-0x1F: TF-A 0x20-0X2F: OPTEE 0x30: Copro |
- ↑ 从报头版本字段的第一个字节到由图像长度字段给定的图像的最后一个字节计算签名。
- ↑ 将所有有效载荷字节的32位总和作为8位无符号数字访问,并丢弃所有溢出位。不使用签名时用于检查下载的图像的完整性。(如果Option标志中的b0 = 1)
- ↑ 长度是构建映像的长度,不包括STM32标头的长度。
- ↑ ROM代码不使用该字段。
- ↑ 图像 版本号 是反回滚的单调计数器。 ROM代码检查它是否大于或等于OTP中存储的单调计数器。
- ↑ 在安全的封闭芯片上必须启用签名验证。
- ↑ 此字段是PEM公钥文件的一部分,该文件仅以原始二进制格式保留ECC点坐标“x”和“y” (RFC 5480).该字段将使用SHA-256进行哈希处理,并与OTP中存储的 公钥的哈希(Hash of pubKey) 进行比较
- ↑ 此填充将STM32标头的大小强制为256个字节(0x100)。
For {{#vardefine:info|}}{{#vardefine:dev|MP15x lines}}{{#vardefine:info| ![]() }}STM32{{#var:dev}}{{#var:info}}:
}}STM32{{#var:dev}}{{#var:info}}:
- the monotonic counter is stored in OTP 4
- the Public Key Hash is stored in OTP WORD 24 to 31
<securetransclude src="ProtectedTemplate:ReviewsComments" params="MCC: is there a tool to read STM32 header fields?"></securetransclude>{{#set:Has reviews comments=true}}
Image programming
Once the images are signed, they can be programmed into the flash on the target board with STM32CubeProgrammer.
PKH check
Before really starting the authentication process, the ROM code compares the hash of the public key carried in the STM32 header with the one that was provisionned in OTP.
Authentication
Bootrom authentication
Using a signed binary, the ROM code authenticates and starts the FSBL.
If the authentication fails, the ROM code enters into a serial boot loop indicated by the blinking Error LED (cf Bootrom common debug and error cases)
The ROM code provides secure services to the FSBL for image authentication with the same ECC pair of keys, so there is no need to support ECDSA algorithm in FSBL.
TF-A authentication
TF-A is the FSBL used by the Trusted boot chain. It is in charge of loading and verifying U-boot and (if used) OP-TEE image binaries.
Each time a signed binary is used, TF-A will print the following status:
INFO: Check signature on Non-Full-Secured platform
If the image authentication fails the boot stage traps the CPU and no more trace is displayed.
Closing the device
Notice that this last step is not shown in the diagram above.
Without any other modification, the device is able to perform image authentication but non authenticated images can still be used and executed: the device is still opened, let's see this as a kind of test mode to check that the PKH is properly set.
As soon as the authentication process is confirmed, the device can be closed and the user forced to use signed images.
OTP WORD0 bit 6 is the OTP bit that closes the device. Burning this bit will lock authentication processing and force authentication from the Boot ROM. Non signed binaries will not be supported anymore on the target.
To program this bit, the STM32CubeProgrammer or U-Boot command line interface can be used.
Here is how to proceed with U-Boot:
Board $> fuse prog 0 0x0 0x40
| Once this bit is written the platform is locked |
<securetransclude src="ProtectedTemplate:PublicationRequestId" params="10394 | 2019-01-30 | BrunoB"></securetransclude>